Hello All
Hope, everyone is doing good. Today we are going to cover the article, about the three Email Authentication Records SPF, DKIM and DMARC which will secure our email environment from the email spoofing and other kinds of attack
In this section, we are going to cover, what is SPF, DKIM and DMARC, how it works , SPF/DMARC syntax, components, and finally implementing SPF and DMARC
Let us first see the SPF , followed by DKIM and DMARC
What is SPF
An SPF record is a TXT record published in the DNS by the domain owner, which specifies a whitelist of IP addresses allowed to send emails on behalf of the domain.
When an email reaches the receiving server, the server will look up the SPF record in the DNS, and perform a check to determine if the email comes from an authorised IP address.
SPF stands for "Sender Policy Framework", which is a mechanism that allows a receiving email server to check if the incoming email is from an IP addresses permitted by a
predefined IP address whitelist (SPF record) specified in the DNS (Domain Name System).
Example : Let us take two organisations craftnet.in and cloudmonkeys.xyz
Domain Name : Crafnet.in
User1@craftnet.in
Application Server : 210.18.121.6
Domain : Cloudmonkeys.xyz
User2@cloudmonkeys.xyz
user1 from craftnet.in is sending an email to user2@cloudmonkeys.xyz from the application server 210.18.121.6 .
It carry's the below information
SPF record syntax
An SPF record is a single string of text published on the domain in the DNS.
All SPF records start with exactly "v=spf1", followed by a series of "terms". Note that the version part "v=spf1" is mandatory: everything else like "v=spf2" would render the SPF record invalid and cause the receiving server to ignore the record.
SPF Record evaluation
An SPF authentication result is one of:
- None: either no valid DNS domain name was found, or no SPF record was found on the domain;
- Neutral: it's not stated whether the client IP address is allowed;
- Pass: the client IP address is allowed;
- Fail: the client IP address is not allowed;
- Softfail: the client IP address is probably not allowed;
SPF qualifiers
An SPF qualifier is optionally prepended to an SPF mechanism to denote the result of evaluating that mechanism.
The possible qualifiers, and the results they indicate are:
- "+" pass
- "-" fail
- "~" softfail
- "?" neutral
For example, qualifier "+" indicates pass, while "-" indicates fail, etc.
SPF mechanisms
SPF mechanisms are evaluated one by one from left to right.
The result of evaluating an SPF mechanism is one of:
- match; evaluation ends and the qualifier value is returned as the result of evaluating the SPF record;
- not match; moves on to evaluate the next mechanism;
- exception; evaluation ends and the exception value is returned.
Two types of SPF mechanisms are available: basic mechanisms and designated sender mechanisms.
Basic mechanisms are all and include.
Designated sender mechanisms are a, mx, ptr, ip4, ip6, and exists.
SPF Check Pass and Fail Scenarios : How to Validate in real time and Troubleshoot
Python script :
I approached some developer team to develop a small script to send an email from python, from which i can test the email to send as an Internal users from internet - simple it works like a application .
So this python application is sending emails from the internet using Internal email address. In Real world , many application is using the email address like no reply@cloudmonkeys.xyz or from active user mailboxes using their party relay or Office SMTP Relay or Relay from Onprem servers if its hybrid setup
my SPF in Go daddy
| v=spf1 ip4:210.18.121.6 include:spf.protection.outlook.com -all It will allow the email only designated from 210.18.121.6 Legitimate email scenario From Internet world, SPF check will pass only if the emails are connected from the designated from connecting IP 210.18.121.6 |
SPF Failed Scenario along with DMARC rule -
if someone sending email which is not designated in the SPF text records and the DMARC rule was set to Reject
What is Domainkeys Identified Mail (DKIM)?
Think of Domainkeys Identified Mail as an ID or passport that can verify who you are. When you are sent from your email server, the server attaches DKIM so the receiving server can verify you.
Technically speaking, DKIM authentication provides a method for validating a domain’s identity that is associated with a message through cryptographic authentication
Lastly, we'll go back to the Defender Portal to enable DKIM for your organization.
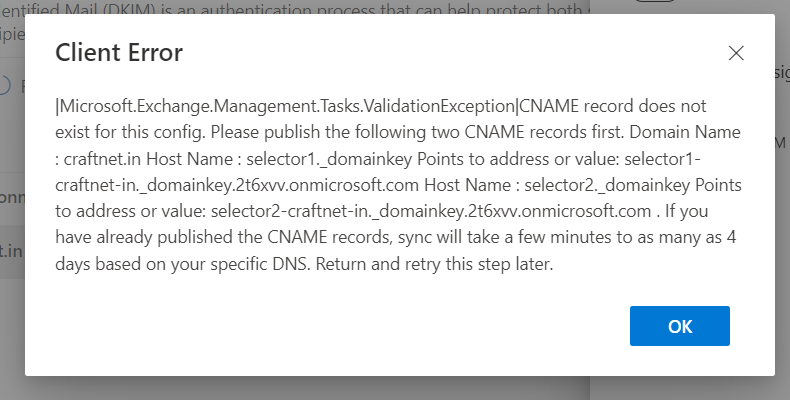
- Sign in to the Microsoft 365 Defender Portal. Use your Microsoft 365 email address and password (your GoDaddy username and password won't work here).
- Under DomainKeys Identified Mail (DKIM), select your domain name. A window will open on the rightmost side.
- Turn on the Sign messages for this domain with DKIM signatures toggle. Your changes will save.
- Select OK.
Domain-based Message Authentication, Reporting, and Conformance DMARC is a widely-accepted email authentication policy and reporting protocol. It ensures – when implemented at an enforcement policy – that authorized use of the domain in the From: field can be verified by the receiving domain and action can be taken if the use is not authorized.
DMARC includes a reporting mechanism. Email receivers tell the domain whether or not the email they received passed or failed authentication. The domain owner’s DMARC record can specify where receivers should send reports—these reports let the domain owner or their DMARC vendor see who is using the domain to send email.
Domain owners can use the information in these reports to fine-tune their email authentication policy to permit only trusted senders to send email on behalf of the domain.
My DMARC Policy in Go daddy
"v=DMARC1; p=reject; pct=100; rua=mailto:aisha.bhari@cloudmonkeys.xyz; ruf=mailto:aisha.bhari@cloudmonkeys.xyz"
Anti phishing Policy Configured in office 365 portal : https://security.microsoft.com/
Exchange Online Message Trace.
In Message Trace, the emails got failed due to DMARC policy
i believe, this article helps for someone who is looking after the SPF, DKIM and DMARC policy implementation in their environment and troubleshooting purpose. Happy learning 😃











Comments
Post a Comment