Hello Everyone.
This is last series on the security operation topic.
Microsoft Defender for EMAIL's
In real world scenario, 91 % of cyber attacks happening in email communications . To protect the email environment, Microsoft defender has Anti-malware, Anti-phishing, safe links, safe attachments, are available to configure in office 365 defender portal, Previously it was know as Microsoft ATP. ( Advanced Threat Protection)
M365 defender uses the multi layered protection Stack in exchange online [email] environment.
Edge Protection : - Also called as outer layer. It check for any network throttling, IP Reputations, Domain reputations, back-scatter detection, and do the enhanced filtering for onprem routing. In real wold , it blocks half of the threats
Sender Intelligence : In this layer , it check for DMARC, DKIM, SPF, Intra-Org Spook intelligence, Cross domain spoof intelligence, bulk filtering, Mailbox intelligence,Mailbox intelligence impersonation, user impersonation, Account Compromise and domain impersonation.
Content Filtering : In this layer, it checks for Transport rules, AV engines, Attachment reputations, URL reputations, Safe attachments, URL detection's.
Post Delivery Protections : i can say this feature is significance improvements in M365 Exchange online protection. It protect the email environment even after the email gets delivered to end user mailbox and it checks for Safe links, Phish Zerohour Auto purge, Malware Zerohour Auto purge, Spam Zerohour Auto purge.
M365 defender detect the threats event the emails are delivered to end user mailbox . This technology is called Post delivery protection or ZAP - Zero Hour Auto purge
Licensing for Microsoft Defender
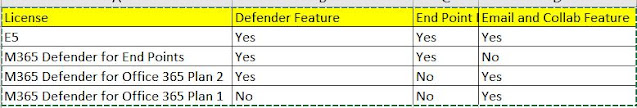
Please go through the below links for the previous post on the same topic's
https://cloudmonkeys20.blogspot.com/2023/01/security-operation-series-part-1.html
https://cloudmonkeys20.blogspot.com/2023/01/security-operation-series-part-2.html
https://cloudmonkeys20.blogspot.com/2023/01/security-operation-series-part-3.html
https://cloudmonkeys20.blogspot.com/2023/02/security-operations-part-4.html
https://cloudmonkeys20.blogspot.com/2023/02/security-operations-part-5.html
https://cloudmonkeys20.blogspot.com/2023/02/security-operation-part-6.html
Comments
Post a Comment